Cisco Catalyst 8000V Edge Softwareを無償でダウンロード/デプロイする方法をご紹介
ダウンロードURL

Cisco Catalyst 8000V Edge Software Free-Trial Offers
Try out Cisco Catalyst 8000V free for 30 days with leading cloud service providers.
前提とメリット
前提
- 30日のトライアルであること
- AWSまたはAzure上で動かす(x86 hardware platform)
メリット
- 最新の8000V EdgeをCLIでコマンド確認ができる
- 比較的新しいios-xe versionが利用可能
- 2022/5/31現在ダウンロード可能 ios-xe version
17.08.01a (May 14,2022)
17.06.03a (May 14,2022)
17.07.01a (Dec 23,2021)
17.06.02 (Dec 01,2021)
17.06.01a (Aug 30,2021)
17.04.02 (Jul 20,2021)
17.05.01a (Apr 27,2021)
17.04.1b (Feb 24,2021)
17.04.1a (Jan 26,2021)
ダウンロードからインストール
Top Page
本ページは、AWSにデプロイする方式で行う。
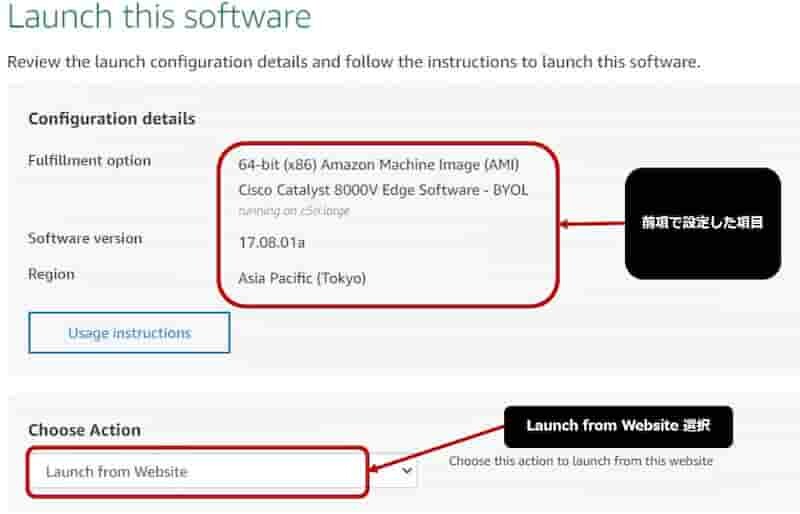
Top pageで [ Catalyst 8000V on Amazon Web Service ] を選択
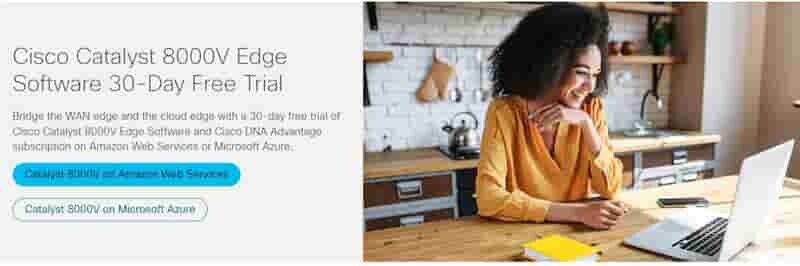
Continue to Subscribe
[ Continue to Subscribe ] をクリック
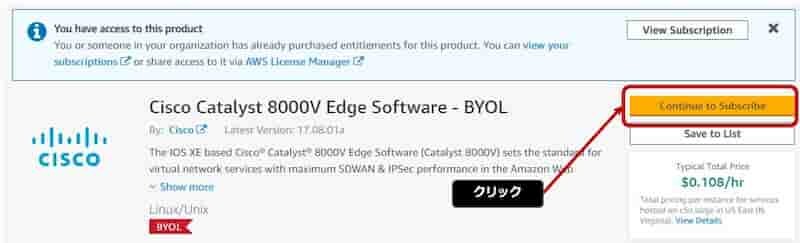
Continue to Configuration
[ Continue to Configuration ] をクリック
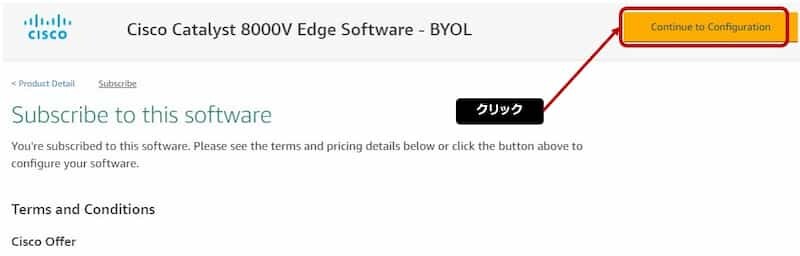
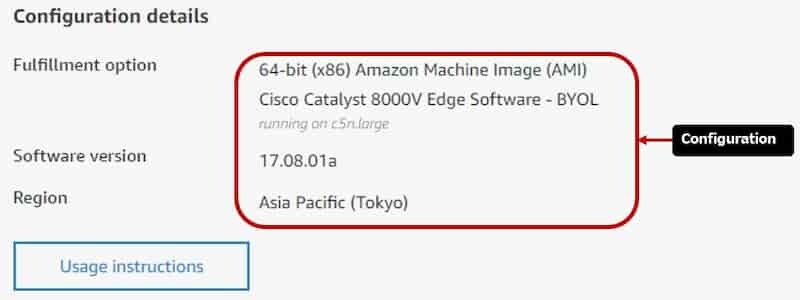
Configure this Software
- 64-bit (x86) Amazon Machine Image (AMI)を選択
- プルダウンで任意のIOS-XEを選択できる
- Tokyo or Osakaを選択
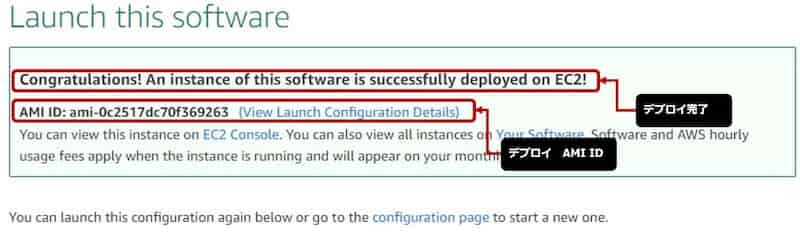
Launch this software
- 前項で決定したAMIを確認
- 前項で決定したIOS-XE Verを確認
- 前項で決定したRegionを確認
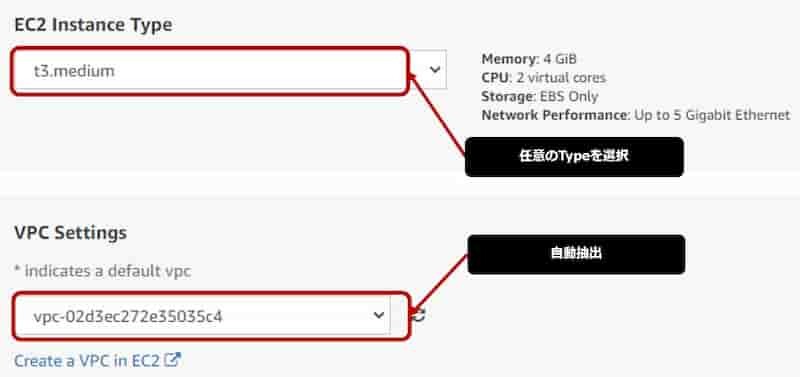
- EC2インスタンスを選択(様々タイプがあるので任意のタイプを選択する)
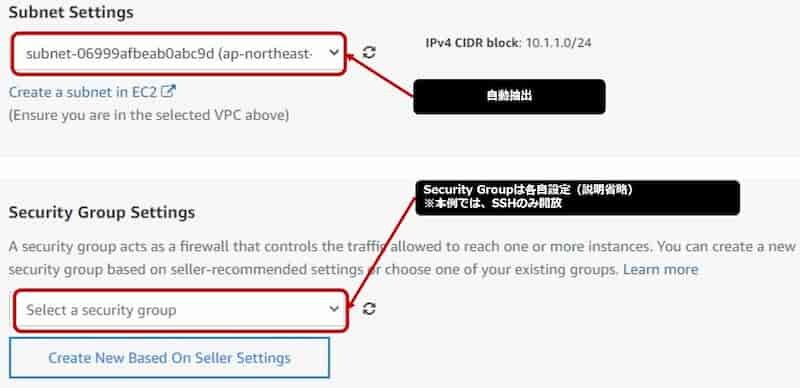
- security groupは未作成になるため作成する
本ページではSSH通信のみpermitし、その他はdenyとする。 - security group作成方法は、AWSの操作になるのでここでは省略する。
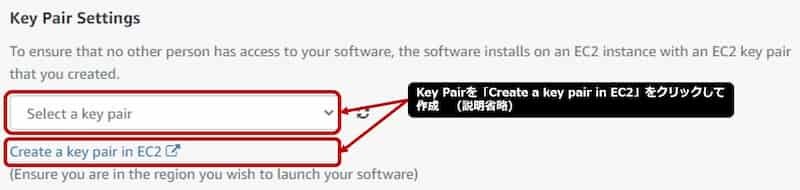
- key pairはSSH接続時必要になるため、[Create a key pair in EC2]をクリックして作成する。
- Key pair作成方法は、AWSの操作になるのでここでは省略する。
- Launch クリック
Launch this software
- Congratulations! An instance of this software is successfully deployed on EC2! 確認
- AMI ID を確認
AWS マネジメントコンソール ログイン
EC2インスタンス確認
1つのEC2インタンスがデプロイされていることを確認する。
![]()
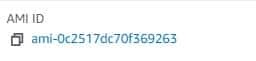
AMI IDとVPC IDを確認しておく
![]()
SSHでEC2インタンスへログイン
- Elastic IPは事前にアタッチする(今回のElastic IP:52.199.207.230)
- Elastic IPアタッチ方法は、AWSの操作になるのでここでは省略する。
- Teratermを開く
- Elastic IPを入力
- サービスをSSH
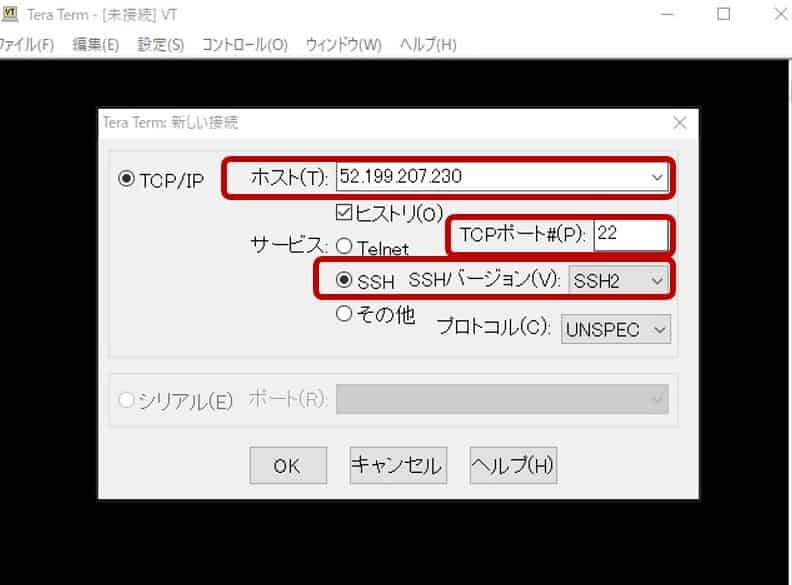
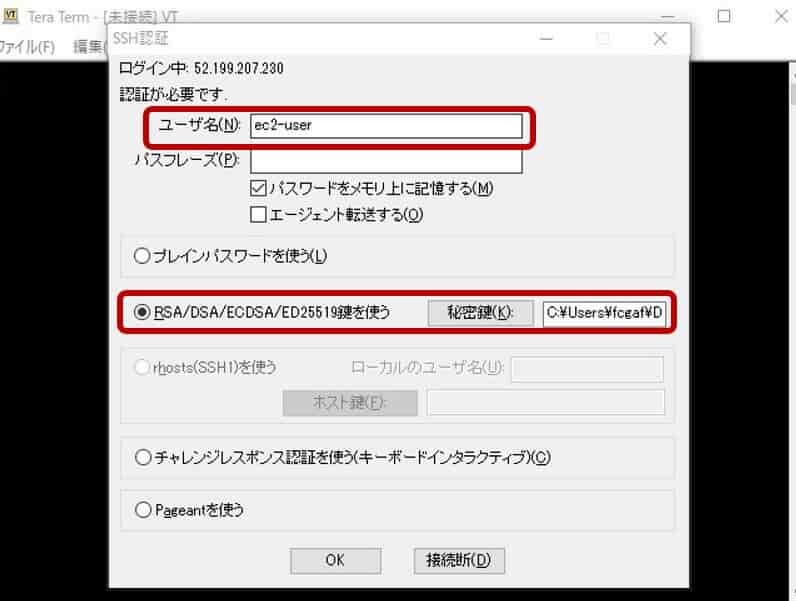
- ユーザID : ec2-user
- パスワード:作成済み key pairファイル選択
ログイン完了
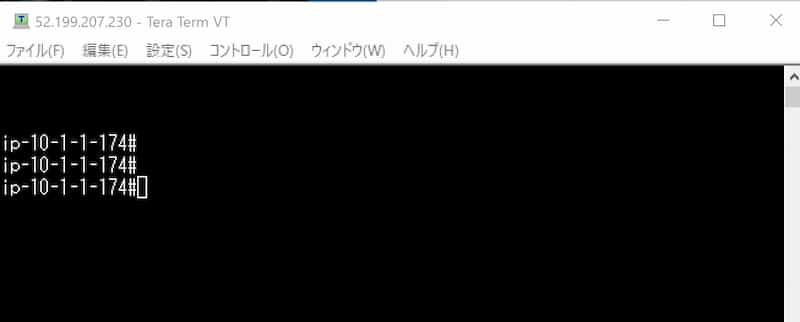
Cisco Catalyst 8000V Edge ログ
show version
ip-10-1-1-174#show ver
Cisco IOS XE Software, Version 17.08.01a
Cisco IOS Software [Cupertino], Virtual XE Software (X86_64_LINUX_IOSD-UNIVERSALK9-M), Version 17.8.1a, RELEASE SOFTWARE (fc3)
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2022 by Cisco Systems, Inc.
Compiled Wed 20-Apr-22 13:09 by mcpre
Cisco IOS-XE software, Copyright (c) 2005-2022 by cisco Systems, Inc.
All rights reserved. Certain components of Cisco IOS-XE software are
licensed under the GNU General Public License ("GPL") Version 2.0. The
software code licensed under GPL Version 2.0 is free software that comes
with ABSOLUTELY NO WARRANTY. You can redistribute and/or modify such
GPL code under the terms of GPL Version 2.0. For more details, see the
documentation or "License Notice" file accompanying the IOS-XE software,
or the applicable URL provided on the flyer accompanying the IOS-XE
software.
ROM: IOS-XE ROMMON
ip-10-1-1-174 uptime is 5 hours, 31 minutes
Uptime for this control processor is 5 hours, 32 minutes
System returned to ROM by reload
System image file is "bootflash:packages.conf"
Last reload reason: Unknown reason
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
If you require further assistance please contact us by sending email to
export@cisco.com.
License Level:
License Type: Perpetual
Next reload license Level:
Addon License Level:
Addon License Type: Subscription
Next reload addon license Level:
The current throughput level is 10000 kbps
Smart Licensing Status: Smart Licensing Using Policy
cisco C8000V (VXE) processor (revision VXE) with 1923579K/3075K bytes of memory.
Processor board ID 90UF6MF1XUD
Router operating mode: Autonomous
1 Gigabit Ethernet interface
32768K bytes of non-volatile configuration memory.
3903740K bytes of physical memory.
11526144K bytes of virtual hard disk at bootflash:.
Configuration register is 0x2102
ip-10-1-1-174#
show run
ip-10-1-1-174#show run Building configuration... Current configuration : 6928 bytes ! ! Last configuration change at 11:21:24 UTC Tue May 31 2022 ! version 17.8 service timestamps debug datetime msec service timestamps log datetime msec service password-encryption ! Call-home is enabled by Smart-Licensing. service call-home platform qfp utilization monitor load 80 platform punt-keepalive disable-kernel-core platform console virtual ! hostname ip-10-1-1-174 ! boot-start-marker boot-end-marker ! ! vrf definition GS rd 100:100 ! address-family ipv4 exit-address-family ! logging persistent size 1000000 filesize 8192 immediate aaa new-model ! ! aaa authentication login default local aaa authorization exec default local none ! ! ! ! ! ! aaa session-id common ! ! ! ! ! ! ! ! ! ! login on-success log ipv6 unicast-routing ! ! ! ! ! ! ! subscriber templating ! multilink bundle-name authenticated ! ! ! crypto pki trustpoint TP-self-signed-1157715532 enrollment selfsigned subject-name cn=IOS-Self-Signed-Certificate-1157715532 revocation-check none rsakeypair TP-self-signed-1157715532 ! crypto pki trustpoint SLA-TrustPoint enrollment pkcs12 revocation-check crl ! ! crypto pki certificate chain TP-self-signed-1157715532 certificate self-signed 01 30820330 30820218 A0030201 02020101 300D0609 2A864886 F70D0101 05050030 31312F30 2D060355 04031326 494F532D 53656C66 2D536967 6E65642D 43657274 69666963 6174652D 31313537 37313535 3332301E 170D3232 30353331 31313231 34305A17 0D333230 35333031 31323134 305A3031 312F302D 06035504 03132649 4F532D53 656C662D 5369676E 65642D43 65727469 66696361 74652D31 31353737 31353533 32308201 22300D06 092A8648 86F70D01 01010500 0382010F 00308201 0A028201 0100AF5E 4C130B68 A296D84D 66413CC0 856CB168 8EA66F72 3BC051E9 1A101C94 580EA52C 97C7999B C630C755 4EB488C0 C51D7024 137D348E 0952DD92 C21B6D13 194183EB 9B17D912 AEBDAB93 588F1DBF 85C38DB6 05145B1C 3C513B69 814C887F 0066E336 2FE724A6 BD3B8D1F 4E4F4EB4 F057E296 2A5DCB7D F052229A 634342C0 D987EA38 3D71507D B0CC2C72 95E5EA2D D0913295 55C12363 9E4F4129 68F59BF0 64DE2290 267549A5 CBECB97C 5F88D30D 3798F8EE 510AAF98 B843890C 5CF47A99 2D9EB580 EA862B54 D79F20A4 092C80CF 78A5EC06 04B052B8 19F3A5EB F6151AAF 9008C503 2C5F6BF4 D37C8D77 A711533E F5FEC0DE 3F5C8C01 59E44F3C 5D94222B 96930203 010001A3 53305130 0F060355 1D130101 FF040530 030101FF 301F0603 551D2304 18301680 14BF43C9 F1962AEC CDF46570 47A3AAAE 1BC08079 F2301D06 03551D0E 04160414 BF43C9F1 962AECCD F4657047 A3AAAE1B C08079F2 300D0609 2A864886 F70D0101 05050003 82010100 41C491F4 BC0ABE2A 5C522CAB 8E4152D0 E4882E38 8B5BF756 D23C40A9 833B402A 323E4301 F330A13B 6D85E7D2 2C4DE16E 749DED50 93D0C52A 0A024E73 B886BC75 3E124899 97F15536 38526159 90C452B7 F0D7FBC0 EDD065E3 6CAACB3D 78A5CBDD DB785739 FC9E1548 89FE2B97 E4359E7D BBFF4555 B0A1AC1D 35EBF4AD 3B9A04FA 4FDB03F4 235B2C68 499798B5 0ADAB2A6 717BCAEF ECDE77D7 B2355265 B582DF08 E5E76939 E4E769A3 9ACAE65A F9E8CF72 1E7B1E7D F1136466 4B8E27CD 36509AD1 B28C2DA3 F006E1AA 9EB5D499 ******** ******** ******** ******** ******** ******** ******** ******* BB8F52EE AD938A3C 27EA59BD 052D25B9 EE9CB839 quit crypto pki certificate chain SLA-TrustPoint certificate ca 01 30820321 30820209 A0030201 02020101 300D0609 2A864886 F70D0101 0B050030 32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720 526F6F74 20434130 1E170D31 33303533 30313934 3834375A 170D3338 30353330 31393438 34375A30 32310E30 0C060355 040A1305 43697363 6F312030 1E060355 04031317 43697363 6F204C69 63656E73 696E6720 526F6F74 20434130 82012230 0D06092A 864886F7 0D010101 05000382 010F0030 82010A02 82010100 A6BCBD96 131E05F7 145EA72C 2CD686E6 17222EA1 F1EFF64D CBB4C798 212AA147 C655D8D7 9471380D 8711441E 1AAF071A 9CAE6388 8A38E520 1C394D78 462EF239 C659F715 B98C0A59 5BBB5CBD 0CFEBEA3 700A8BF7 D8F256EE 4AA4E80D DB6FD1C9 60B1FD18 FFC69C96 6FA68957 A2617DE7 104FDC5F EA2956AC 7390A3EB 2B5436AD C847A2C5 DAB553EB 69A9A535 58E9F3E3 C0BD23CF 58BD7188 68E69491 20F320E7 948E71D7 AE3BCC84 F10684C7 4BC8E00F 539BA42B 42C68BB7 C7479096 B4CB2D62 EA2F505D C7B062A4 6811D95B E8250FC4 5D5D5FB8 8F27D191 C55F0D76 61F9A4CD 3D992327 A8BB03BD 4E6D7069 7CBADF8B DF5F4368 95135E44 DFC7C6CF 04DD7FD1 02030100 01A34230 40300E06 03551D0F 0101FF04 04030201 06300F06 03551D13 0101FF04 05300301 01FF301D 0603551D 0E041604 1449DC85 ******** ******** ******** ******** ******** ******** ******** ******** D697DF7F 28 quit ! license udi pid C8000V sn 90UF6MF1XUD diagnostic bootup level minimal memory free low-watermark processor 64139 ! ! ! ! username ec2-user privilege 15 ! redundancy ! ! ! ! ! ! ! ! interface VirtualPortGroup0 vrf forwarding GS ip address 192.168.35.101 255.255.255.0 ip nat inside ! interface GigabitEthernet1 ip address dhcp ip nat outside negotiation auto ipv6 address dhcp ipv6 enable ipv6 nd autoconfig default-route ! iox ip forward-protocol nd ip tcp window-size 8192 ip http server ip http secure-server ! ip nat inside source list GS_NAT_ACL interface GigabitEthernet1 vrf GS overload ip route 0.0.0.0 0.0.0.0 GigabitEthernet1 10.1.1.1 ip route vrf GS 0.0.0.0 0.0.0.0 GigabitEthernet1 10.1.1.1 global ip ssh rsa keypair-name ssh-key ip ssh version 2 ip ssh pubkey-chain username ec2-user key-hash ssh-rsa D45C10C35D50E879DFC1A09C9B00453B ec2-user ip ssh server algorithm publickey ecdsa-sha2-nistp256 ecdsa-sha2-nistp384 ecdsa-sha2-nistp521 ssh-rsa x509v3-ecdsa-sha2-nistp256 x509v3-ecdsa-sha2-nistp384 x509v3-ecdsa-sha2-nistp521 ip scp server enable ! ip access-list standard GS_NAT_ACL 10 permit 192.168.35.0 0.0.0.255 ! ! ! ! ! ! ! control-plane ! ! line con 0 stopbits 1 line aux 0 line vty 0 4 transport input ssh line vty 5 20 transport input ssh ! call-home ! If contact email address in call-home is configured as sch-smart-licensing@cisco.com ! the email address configured in Cisco Smart License Portal will be used as contact email address to send SCH notifications. contact-email-addr sch-smart-licensing@cisco.com profile "CiscoTAC-1" active destination transport-method http ! ! ! ! ! ! app-hosting appid guestshell app-vnic gateway1 virtualportgroup 0 guest-interface 0 guest-ipaddress 192.168.35.102 netmask 255.255.255.0 app-default-gateway 192.168.35.101 guest-interface 0 name-server0 8.8.8.8 end ip-10-1-1-174#


