Cisco CMLを使って[GRE over IPSec ] の構成を作成、検証をします。
また、[GRE over IPSec ]はPPPoEを越しに利用されていることも多いことからPPPoE Serverも検証環境に盛り込んでいます。
掲載したコンフィグをそのままコピペすればすぐに構築できるようにしています。
NW構成
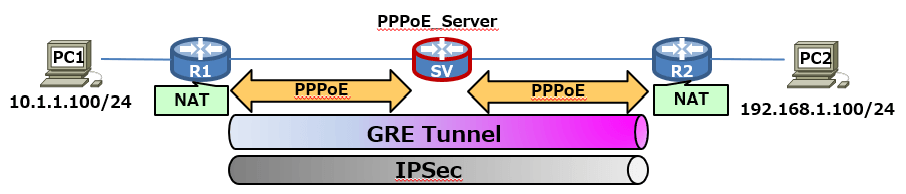
| R1 | Tunnel0 | 9.9.9.1/24 |
| GigabitEthernet0/0 | 1.1.1.1/32 (PPPoE) | |
| GigabitEthernet0/1 | 10.1.1.254/24 | |
| ospf | network 10.1.1.0 0.0.0.255 area 0 |
| R2 | Tunnel0 | 9.9.9.2/24 |
| GigabitEthernet0/0 | 2.2.2.2/32 (PPPoE) | |
| GigabitEthernet0/1 | 192.168.1.254/24 | |
| ospf | network 192.168.1.0 0.0.0.255 area 0 |
各ルータコンフィグ
R1-Config
hostname R1
!
crypto isakmp policy 100
encr aes
hash sha256
authentication pre-share
group 2
lifetime 1800
crypto isakmp key PS-key address 2.2.2.2
crypto isakmp keepalive 30 periodic
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha256-hmac
mode transport
!
!
!
crypto map Crypto_MAP 200 ipsec-isakmp
set peer 2.2.2.2
set security-association lifetime seconds 1200
set transform-set TRANSFORM-SET
set pfs group14
match address Tunnel2Tunnel
!
!
!
!
!
interface Tunnel0
ip address 9.9.9.1 255.255.255.0
ip tcp adjust-mss 1350
ip ospf 1 area 0
tunnel source Dialer1
tunnel destination 2.2.2.2
!
interface GigabitEthernet0/0
no ip address
ip mtu 1492
duplex auto
speed auto
media-type rj45
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface GigabitEthernet0/1
ip address 10.1.1.254 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
interface Dialer1
mtu 1492
ip address negotiated
ip access-group ISAKMP&ESP in
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer-group 1
ppp authentication chap callin
ppp chap hostname r1@pppoe.com
ppp chap password 0 p@ss-r1
crypto map Crypto_MAP
!
router ospf 1
network 10.1.1.0 0.0.0.255 area 0
!
ip nat inside source list NAT-INSIDE interface Dialer1 overload
ip route 0.0.0.0 0.0.0.0 Dialer1
!
ip access-list standard NAT-INSIDE
permit 10.1.1.0 0.0.0.255
!
ip access-list extended ISAKMP&ESP
permit udp host 2.2.2.2 eq isakmp host 1.1.1.1
permit esp host 2.2.2.2 host 1.1.1.1
ip access-list extended Tunnel2Tunnel
permit gre host 1.1.1.1 host 2.2.2.2
!
dialer-list 1 protocol ip permit
!
control-plane
!
end
R1#
R2-Config
hostname R2
!
crypto isakmp policy 100
encr aes
hash sha256
authentication pre-share
group 2
lifetime 1800
crypto isakmp key PS-key address 1.1.1.1
crypto isakmp keepalive 30 periodic
!
!
crypto ipsec transform-set TRANSFORM-SET esp-aes esp-sha256-hmac
mode transport
!
!
!
crypto map Crypto_MAP 200 ipsec-isakmp
set peer 1.1.1.1
set security-association lifetime seconds 1200
set transform-set TRANSFORM-SET
set pfs group14
match address Tunnel2Tunnel
!
!
!
!
!
interface Tunnel0
ip address 9.9.9.3 255.255.255.0
ip tcp adjust-mss 1350
ip ospf 1 area 0
tunnel source Dialer1
tunnel destination 1.1.1.1
!
interface GigabitEthernet0/0
no ip address
ip mtu 1492
duplex auto
speed auto
media-type rj45
pppoe enable group global
pppoe-client dial-pool-number 1
!
interface GigabitEthernet0/1
ip address 192.168.1.254 255.255.255.0
ip nat inside
ip virtual-reassembly in
duplex auto
speed auto
media-type rj45
!
interface Dialer1
mtu 1492
ip address negotiated
ip access-group ISAKMP&ESP in
ip nat outside
ip virtual-reassembly in
encapsulation ppp
dialer pool 1
dialer-group 1
ppp authentication chap callin
ppp chap hostname r2@pppoe.com
ppp chap password 0 p@ss-r2
crypto map Crypto_MAP
!
router ospf 1
network 192.168.1.0 0.0.0.255 area 0
!
ip nat inside source list NAT-INSIDE interface Dialer1 overload
ip route 0.0.0.0 0.0.0.0 Dialer1
!
ip access-list standard NAT-INSIDE
permit 192.168.1.0 0.0.0.255
!
ip access-list extended ISAKMP&ESP
permit udp host 1.1.1.1 eq isakmp host 2.2.2.2
permit esp host 1.1.1.1 host 2.2.2.2
ip access-list extended Tunnel2Tunnel
permit gre host 2.2.2.2 host 1.1.1.1
!
dialer-list 1 protocol ip permit
!
control-plane
!
end
R2#
PPPoE_SV-Config
hostname PPPoE_SV
!
username r1@pppoe.com password 0 p@ss-r1
username r2@pppoe.com password 0 p@ss-r2
!
bba-group pppoe R1_bba1
virtual-template 1
!
bba-group pppoe R2_bba2
virtual-template 2
!
!
interface Loopback1
ip address 172.16.1.1 255.255.255.255
!
interface Loopback2
ip address 172.16.2.1 255.255.255.255
!
interface GigabitEthernet0/0
description To-R1_PPPoE
no ip address
pppoe enable group R1_bba1
!
interface GigabitEthernet0/1
description To-R2_PPPoE
no ip address
pppoe enable group R2_bba2
!
interface Virtual-Template1
description pppoe R1_bba1
mtu 1454
ip unnumbered Loopback1
peer default ip address pool pool1
ppp authentication chap
!
interface Virtual-Template2
description pppoe R2_bba2
mtu 1454
ip unnumbered Loopback2
peer default ip address pool pool2
ppp authentication chap
!
ip local pool pool1 1.1.1.1
ip local pool pool2 2.2.2.2
!
control-plane
!
end
PPPoE_SV#
ログ確認
show crypto isakmp saの場合
R1 show crypto isakmp sa (正常時)
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
2.2.2.2 1.1.1.1 QM_IDLE 1010 ACTIVE
1.1.1.1 2.2.2.2 QM_IDLE 1009 ACTIVE
R2 show crypto isakmp sa (正常時)
R2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
2.2.2.2 1.1.1.1 QM_IDLE 1009 ACTIVE
1.1.1.1 2.2.2.2 QM_IDLE 1010 ACTIVE
R1 show crypto isakmp sa (設定不備時)
※tunnel destinationを誤って設定にした場合
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
IPv6 Crypto ISAKMP SA
R1#
R2 show crypto isakmp sa (設定不備時)
※tunnel destinationを誤って設定にした場合
R2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
IPv6 Crypto ISAKMP SA
R2#
show crypto ipsec saの場合
R1 show crypto ipsec sa (正常時)
R1#show crypto ipsec sa
interface: Dialer1
Crypto map tag: Crypto_MAP, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
current_peer 2.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 110, #pkts encrypt: 110, #pkts digest: 110
#pkts decaps: 109, #pkts decrypt: 109, #pkts verify: 109
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 2.2.2.2
plaintext mtu 1442, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0x60576846(1616341062)
PFS (Y/N): Y, DH group: group14
inbound esp sas:
spi: 0xAC4ACF(11291343)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Transport, }
conn id: 1, flow_id: SW:1, sibling_flags 80000000, crypto map: Crypto_MAP
sa timing: remaining key lifetime (k/sec): (4198293/1104)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x60576846(1616341062)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Transport, }
conn id: 2, flow_id: SW:2, sibling_flags 80000000, crypto map: Crypto_MAP
sa timing: remaining key lifetime (k/sec): (4198293/1104)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R1#
R2 show crypto ipsec sa (正常時)
R2#show crypto ipsec sa
interface: Dialer1
Crypto map tag: Crypto_MAP, local addr 2.2.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
current_peer 1.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 148, #pkts encrypt: 148, #pkts digest: 148
#pkts decaps: 150, #pkts decrypt: 150, #pkts verify: 150
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.2.2, remote crypto endpt.: 1.1.1.1
plaintext mtu 1442, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0xAC4ACF(11291343)
PFS (Y/N): Y, DH group: group14
inbound esp sas:
spi: 0x60576846(1616341062)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Transport, }
conn id: 1, flow_id: SW:1, sibling_flags 80004000, crypto map: Crypto_MAP
sa timing: remaining key lifetime (k/sec): (4277335/1072)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xAC4ACF(11291343)
transform: esp-aes esp-sha256-hmac ,
in use settings ={Transport, }
conn id: 2, flow_id: SW:2, sibling_flags 80004000, crypto map: Crypto_MAP
sa timing: remaining key lifetime (k/sec): (4277336/1072)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R2#
R1 show crypto ipsec sa (設定不備時)
※tunnel destinationを誤って設定にした場合
R1#show crypto ipsec sa
interface: Dialer1
Crypto map tag: Crypto_MAP, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
current_peer 2.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 2.2.2.2
plaintext mtu 1492, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
R1#
R2 show crypto ipsec sa (設定不備時)
※tunnel destinationを誤って設定にした場合
R2#show crypto ipsec sa
interface: Dialer1
Crypto map tag: Crypto_MAP, local addr 2.2.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
current_peer 1.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 0, #pkts encrypt: 0, #pkts digest: 0
#pkts decaps: 0, #pkts decrypt: 0, #pkts verify: 0
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.2.2, remote crypto endpt.: 1.1.1.1
plaintext mtu 1492, path mtu 1492, ip mtu 1492, ip mtu idb Dialer1
current outbound spi: 0x0(0)
PFS (Y/N): N, DH group: none
inbound esp sas:
inbound ah sas:
inbound pcp sas:
outbound esp sas:
outbound ah sas:
outbound pcp sas:
R2#
ルーティングテーブル
パケットキャプチャによる暗号化確認

| R1 | Tunnel0 | 9.9.9.1/24 |
| GigabitEthernet0/0 | 1.1.1.1/32 (PPPoE) | |
| GigabitEthernet0/1 | 10.1.1.254/24 | |
| ospf | network 10.1.1.0 0.0.0.255 area 0 |
| R2 | Tunnel0 | 9.9.9.2/24 |
| GigabitEthernet0/0 | 2.2.2.2/32 (PPPoE) | |
| GigabitEthernet0/1 | 192.168.1.254/24 | |
| ospf | network 192.168.1.0 0.0.0.255 area 0 |
■キャプチャポイント
R1とPPPoE-SV間
■確認するパケット
PC1 ⇒ PC2にPingを送信した時のパケットキャプチャを確認する。
■Protocol
ESPになっていること(暗号化されていること)
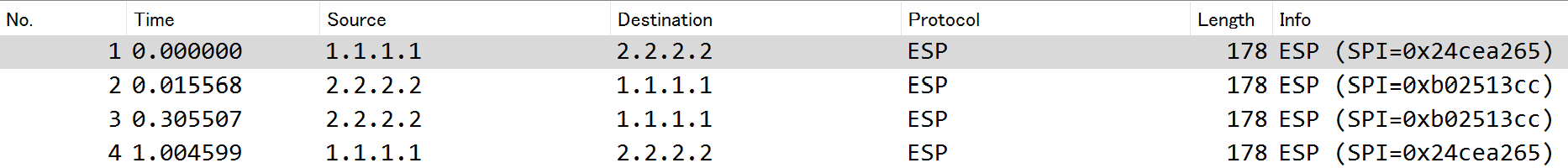
ProtocolがESPでなく、ICMPとなる場合は暗号化されていないので、その場合は設定の誤りを確認すべきです。


