【概要】
・Cisco機器のIPsec VPN参考コンフィグを掲載
・暗号化されていることをログ確認
・暗号化されていることをパケットキャプチャ確認
構成図(CMLで構成)
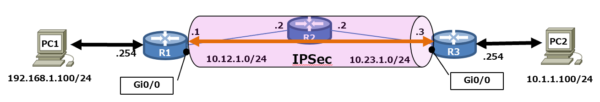
- PC1 ⇔ PC2 間の通信において、R1 ⇔ R3間でパケットを暗号化
(黒矢印部分は平文、オレンジ矢印部分は暗号化) - ESP暗号化: esp-aes 256
- ESP認証:esp-sha512-hmac
- Preshared-key: P@SSWD
Config例
IPsec Tunnel mode
R1-config <click!>
hostname R1 ! crypto isakmp policy 1 encr aes 256 hash sha512 authentication pre-share group 5 crypto isakmp key P@SSWD address 10.23.1.3 ! crypto ipsec transform-set TF-SET esp-aes 256 esp-sha512-hmac mode tunnel ! crypto map CRYPTO 50 ipsec-isakmp set peer 10.23.1.3 set transform-set TF-SET set pfs group5 match address 100 ! interface GigabitEthernet0/0 ip address 10.12.1.1 255.255.255.0 crypto map CRYPTO ! interface GigabitEthernet0/1 ip address 192.168.1.254 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 10.12.1.2 ! access-list 100 permit ip host 192.168.1.100 host 10.1.1.100 ! control-plane ! end
R2-config <click!>
hostname R2 ! interface GigabitEthernet0/0 ip address 10.12.1.2 255.255.255.0 ! interface GigabitEthernet0/1 ip address 10.23.1.2 255.255.255.0 ! control-plane ! end
R3-config <click!>
hostname R3 ! crypto isakmp policy 1 encr aes 256 hash sha512 authentication pre-share group 5 crypto isakmp key P@SSWD address 10.12.1.1 ! crypto ipsec transform-set TF-SET esp-aes 256 esp-sha512-hmac mode tunnel ! crypto map CRYPTO 50 ipsec-isakmp set peer 10.12.1.1 set transform-set TF-SET set pfs group5 match address 100 ! interface GigabitEthernet0/0 ip address 10.23.1.3 255.255.255.0 crypto map CRYPTO ! interface GigabitEthernet0/1 ip address 10.1.1.254 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 10.23.1.2 ! access-list 100 permit ip host 10.1.1.100 host 192.168.1.100 ! control-plane ! end
IPsec動作確認ログ
IPsecを設定しても本当に暗号化されているか確証がないためログの確認が必要です。
show ip interface brief
- NVIインターフェイスを確認
R1_log
R1#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 10.12.1.1 YES NVRAM up up
GigabitEthernet0/1 192.168.1.254 YES NVRAM up up
NVI0 10.12.1.1 YES unset up up
R3_log
R3#show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 10.23.1.3 YES NVRAM up up
GigabitEthernet0/1 10.1.1.254 YES NVRAM up up
NVI0 10.23.1.3 YES unset up up
show crypto isakmp sa
- ISAKMP SAの確立の確認(state:QM_IDLE)
R1_log
R1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 10.23.1.3 10.12.1.1 QM_IDLE 1001 ACTIVE
R3_log
R3#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 10.23.1.3 10.12.1.1 QM_IDLE 1001 ACTIVE
show crypto isakmp policy
- 設定内容の確認
- SAのライフタイムは86400 (24時間) デフォルト
R1_log
R1#show crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard 2 (512 bit)
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 86400 seconds, no volume limit
R3_log
R3#show crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: AES - Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard 2 (512 bit)
authentication method: Pre-Shared Key
Diffie-Hellman group: #5 (1536 bit)
lifetime: 86400 seconds, no volume limit
show crypto session
- Session status が「UP-ACTIVE」になること
R1_log
R1#show crypto session
Crypto session current status
Interface: GigabitEthernet0/0
Session status: UP-ACTIVE
Peer: 10.23.1.3 port 500
Session ID: 0
IKEv1 SA: local 10.12.1.1/500 remote 10.23.1.3/500 Active
IPSEC FLOW: permit ip host 192.168.1.100 host 10.1.1.100
Active SAs: 2, origin: crypto map
R3_log
R3#show crypto session
Crypto session current status
Interface: GigabitEthernet0/0
Session status: UP-ACTIVE
Peer: 10.12.1.1 port 500
Session ID: 0
IKEv1 SA: local 10.23.1.3/500 remote 10.12.1.1/500 Active
IPSEC FLOW: permit ip host 10.1.1.100 host 192.168.1.100
Active SAs: 2, origin: crypto map
パケットキャプチャ
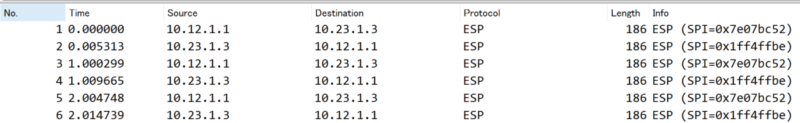
PC1 ⇒ PC2へ継続的にpingを実施し、R1 ⇔ R2間でパケットキャプチャをして暗号化されている確認します。
暗号化されていない場合、ProtocolはICMPになりますが、暗号化されていることによりESPになり暗号化されていることがわかります。