<概要>
- DynamicでMultipointにVPN構成を組むことが可能
- 論理的にフルメッシュになる
- GRE Tunnelを利用し、IPSecで暗号化する
- GRE Tunnel内で利用可能なルーティングプロトコル(RIP/EIGRP/OSPF/BGP等々)
- NHRP (Next Hop Resolution Protocol)によりServer/Clientを構成する
- 1つのルータがNHRP_Serverになり、その他全ルータがNHRP Clientになる
構成図
構成
- Hub1_Router = NHRP_Server
- Spoke1/2/3_Router = NHRP_Client
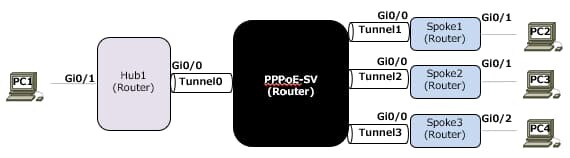
- NHRP_Clientは、NHRP-Serverの[Global IP]と[Tunnel IP]をstaticで設定する必要がある。
- 各セグメント間のDynamic RoutingはOSPFを利用する。
通信経路
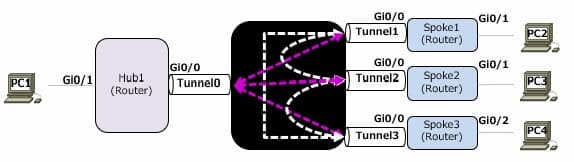
パラメータ

PC2 -> PC1通信
Spoke1(NHRP_Client)の設定上、Hub1(NHRP_Server)の[Global IP]と[Tunnel IP]が設定されているため
それを利用して通信を行う。
PC2 -> PC3通信
Spoke1(NHRP_Client)はHub1(NHRP_Server)にSpoke2の[Global IP]をリクエストすることにより
Hub1を経由することなく、1対1で通信できる
Config <Cisco CML>
Hub1-config <click>
hostname Hub1 ! crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 ! crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac mode transport ! crypto ipsec profile profile-dmvpn set transform-set transform-dmvpn ! interface Tunnel0 bandwidth 1000 ip address 10.0.0.1 255.255.255.0 no ip redirects ip mtu 1400 ip nhrp authentication test ip nhrp network-id 100000 ip tcp adjust-mss 1360 ip ospf network broadcast delay 1000 tunnel source Dialer1 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile profile-dmvpn ! interface GigabitEthernet0/0 no ip address pppoe enable group global pppoe-client dial-pool-number 1 ! interface GigabitEthernet0/1 ip address 192.168.1.254 255.255.255.0 ! interface Dialer1 mtu 1454 ip address negotiated encapsulation ppp dialer pool 1 dialer-group 1 ppp authentication chap callin ppp chap hostname r1@pppoe.com ppp chap password 0 p@ss-r1 ! router ospf 1 passive-interface GigabitEthernet0/1 network 10.0.0.0 0.0.0.255 area 0 network 192.168.1.0 0.0.0.255 area 0 ! ip route 0.0.0.0 0.0.0.0 Dialer1 ! dialer-list 1 protocol ip permit ! control-plane ! end
Spoke1-config <click>
hostname Spoke1 ! crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 ! crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac mode transport ! crypto ipsec profile profile-dmvpn set transform-set transform-dmvpn ! interface Tunnel1 bandwidth 1000 ip address 10.0.0.2 255.255.255.0 no ip redirects ip mtu 1400 ip nhrp authentication test ip nhrp map 10.0.0.1 1.1.1.1 ip nhrp map multicast 1.1.1.1 ip nhrp network-id 100000 ip nhrp holdtime 300 ip nhrp nhs 10.0.0.1 ip tcp adjust-mss 1360 ip ospf network broadcast ip ospf priority 0 tunnel source Dialer1 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile profile-dmvpn ! interface GigabitEthernet0/0 no ip address ip mtu 1492 pppoe enable group global pppoe-client dial-pool-number 1 ! interface GigabitEthernet0/1 ip address 192.168.2.254 255.255.255.0 ! interface Dialer1 mtu 1454 ip address negotiated encapsulation ppp dialer pool 1 dialer-group 1 ppp authentication chap callin ppp chap hostname r2@pppoe.com ppp chap password 0 p@ss-r2 ! router ospf 1 passive-interface GigabitEthernet0/1 network 10.0.0.0 0.0.0.255 area 0 network 192.168.2.0 0.0.0.255 area 0 ! ip route 0.0.0.0 0.0.0.0 Dialer1 ! dialer-list 1 protocol ip permit ! control-plane ! end
Spoke2-config <click>
hostname Spoke2 ! crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 ! crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac mode transport ! crypto ipsec profile profile-dmvpn set transform-set transform-dmvpn ! interface Tunnel2 bandwidth 1000 ip address 10.0.0.3 255.255.255.0 no ip redirects ip mtu 1400 ip nhrp authentication test ip nhrp map 10.0.0.1 1.1.1.1 ip nhrp map multicast 1.1.1.1 ip nhrp network-id 100000 ip nhrp holdtime 300 ip nhrp nhs 10.0.0.1 ip tcp adjust-mss 1360 ip ospf network broadcast ip ospf priority 0 tunnel source Dialer1 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile profile-dmvpn ! interface GigabitEthernet0/0 no ip address ip mtu 1492 duplex auto speed auto media-type rj45 pppoe enable group global pppoe-client dial-pool-number 1 ! interface GigabitEthernet0/1 ip address 192.168.3.254 255.255.255.0 ! interface Dialer1 mtu 1454 ip address negotiated encapsulation ppp dialer pool 1 dialer-group 1 ppp authentication chap callin ppp chap hostname r3@pppoe.com ppp chap password 0 p@ss-r3 ! router ospf 1 passive-interface GigabitEthernet0/1 network 10.0.0.0 0.0.0.255 area 0 network 192.168.3.0 0.0.0.255 area 0 ! ip route 0.0.0.0 0.0.0.0 Dialer1 ! dialer-list 1 protocol ip permit ! control-plane ! end
Spoke3-config <click>
hostname Spoke3 ! crypto isakmp policy 1 encr aes 256 hash sha256 authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 ! crypto ipsec transform-set transform-dmvpn esp-aes 256 esp-sha-hmac mode transport ! crypto ipsec profile profile-dmvpn set transform-set transform-dmvpn ! interface Tunnel3 bandwidth 1000 ip address 10.0.0.4 255.255.255.0 no ip redirects ip mtu 1400 ip nhrp authentication test ip nhrp map 10.0.0.1 1.1.1.1 ip nhrp map multicast 1.1.1.1 ip nhrp network-id 100000 ip nhrp holdtime 300 ip nhrp nhs 10.0.0.1 ip tcp adjust-mss 1360 ip ospf network broadcast ip ospf priority 0 tunnel source Dialer1 tunnel mode gre multipoint tunnel key 100000 tunnel protection ipsec profile profile-dmvpn ! interface GigabitEthernet0/0 no ip address ip mtu 1492 pppoe enable group global pppoe-client dial-pool-number 1 ! interface GigabitEthernet0/1 ip address 192.168.4.254 255.255.255.0 ! interface Dialer1 mtu 1454 ip address negotiated encapsulation ppp dialer pool 1 dialer-group 1 ppp authentication chap callin ppp chap hostname r4@pppoe.com ppp chap password 0 p@ss-r4 ! router ospf 1 passive-interface GigabitEthernet0/1 network 10.0.0.0 0.0.0.255 area 0 network 192.168.4.0 0.0.0.255 area 0 ! ip forward-protocol nd ! ip route 0.0.0.0 0.0.0.0 Dialer1 ! dialer-list 1 protocol ip permit ! control-plane ! end
PPPoE-SV-config <click>
hostname PPPoE-SV ! username r1@pppoe.com password 0 p@ss-r1 username r2@pppoe.com password 0 p@ss-r2 username r3@pppoe.com password 0 p@ss-r3 username r4@pppoe.com password 0 p@ss-r4 ! bba-group pppoe R1 virtual-template 1 ! bba-group pppoe R2 virtual-template 2 ! bba-group pppoe R3 virtual-template 3 ! bba-group pppoe R4 virtual-template 4 ! interface GigabitEthernet0/0 no ip address duplex auto speed auto media-type rj45 pppoe enable group R1 ! interface GigabitEthernet0/1 no ip address duplex auto speed auto media-type rj45 pppoe enable group R2 ! interface GigabitEthernet0/2 no ip address duplex auto speed auto media-type rj45 pppoe enable group R3 ! interface GigabitEthernet0/3 no ip address duplex auto speed auto media-type rj45 pppoe enable group R4 ! interface Virtual-Template1 mtu 1454 ip address 1.1.1.254 255.255.255.0 peer default ip address pool pool1 ppp authentication chap ! interface Virtual-Template2 mtu 1454 ip address 2.2.2.254 255.255.255.0 peer default ip address pool pool2 ppp authentication chap ! interface Virtual-Template3 mtu 1454 ip address 3.3.3.254 255.255.255.0 peer default ip address pool pool3 ppp authentication chap ! interface Virtual-Template4 mtu 1454 ip address 4.4.4.254 255.255.255.0 peer default ip address pool pool4 ppp authentication chap ! ip local pool pool1 1.1.1.1 ip local pool pool2 2.2.2.2 ip local pool pool3 3.3.3.3 ip local pool pool4 4.4.4.4 ! control-plane ! end
ルーティングテーブル (show ip route ospf)
Hub1#show ip route ospf Gateway of last resort is 0.0.0.0 to network 0.0.0.0 O 192.168.2.0/24 [110/101] via 10.0.0.2, 02:05:35, Tunnel0 O 192.168.3.0/24 [110/101] via 10.0.0.3, 02:05:35, Tunnel0 O 192.168.4.0/24 [110/101] via 10.0.0.4, 02:05:35, Tunnel0
Spoke1#show ip route ospf Gateway of last resort is 0.0.0.0 to network 0.0.0.0 O 192.168.1.0/24 [110/101] via 10.0.0.1, 02:05:40, Tunnel1 O 192.168.3.0/24 [110/101] via 10.0.0.3, 02:05:30, Tunnel1 O 192.168.4.0/24 [110/101] via 10.0.0.4, 02:05:40, Tunnel1
Spoke2#show ip route ospf Gateway of last resort is 0.0.0.0 to network 0.0.0.0 O 192.168.1.0/24 [110/101] via 10.0.0.1, 02:05:55, Tunnel2 O 192.168.2.0/24 [110/101] via 10.0.0.2, 02:05:55, Tunnel2 O 192.168.4.0/24 [110/101] via 10.0.0.4, 02:05:55, Tunnel2
Spoke3#show ip route ospf Gateway of last resort is 0.0.0.0 to network 0.0.0.0 O 192.168.1.0/24 [110/101] via 10.0.0.1, 02:05:59, Tunnel3 O 192.168.2.0/24 [110/101] via 10.0.0.2, 02:05:59, Tunnel3 O 192.168.3.0/24 [110/101] via 10.0.0.3, 02:05:59, Tunnel3
PC2からのTraceroute
PC2 ⇒ PC1 <click>
PC2:~$ traceroute 192.168.1.1 traceroute to 192.168.1.1 (192.168.1.1), 30 hops max, 46 byte packets 1 192.168.2.254 (192.168.2.254) 3.280 ms 3.686 ms 3.168 ms 2 10.0.0.1 (10.0.0.1) 11.906 ms 19.962 ms 13.846 ms 3 192.168.1.1 (192.168.1.1) 18.912 ms 11.106 ms 12.030 ms
PC2 ⇒ PC3 <click>
PC2:~$ traceroute 192.168.3.1
traceroute to 192.168.3.1 (192.168.3.1), 30 hops max, 46 byte packets
1 192.168.2.254 (192.168.2.254) 2.934 ms 5.461 ms 9.655 ms
2 10.0.0.3 (10.0.0.3) 16.005 ms 11.013 ms
3 192.168.3.1 (192.168.3.1) 10.688 ms 11.681 ms 10.448 ms
PC2 ⇒ PC4 <click>
PC2:~$ traceroute 192.168.4.1
traceroute to 192.168.4.1 (192.168.4.1), 30 hops max, 46 byte packets
1 192.168.2.254 (192.168.2.254) 3.154 ms 3.423 ms 1.999 ms
2 10.0.0.4 (10.0.0.4) 11.094 ms 17.506 ms
3 192.168.4.1 (192.168.4.1) 12.683 ms 15.172 ms 17.866 ms
各種show コマンド結果
Hub1/Spoke1: show ip nhrp brief
Hub1-show ip nhrp brief <click>
Hub1#show ip nhrp brief
Legend: Type --> S - Static, D - Dynamic
Flags --> u - unique, r - registered, e - temporary, c - claimed
a - authoritative, t - route
============================================================================
Intf NextHop Address NBMA Address
Target Network T/Flag
-------- ------------------------------------------- ------ ----------------
Tu0 10.0.0.2 2.2.2.2
10.0.0.2/32 D/r
Tu0 10.0.0.3 3.3.3.3
10.0.0.3/32 D/r
Tu0 10.0.0.4 4.4.4.4
10.0.0.4/32 D/r
Spoke1-show ip nhrp brief <click>
Spoke1#show ip nhrp brief
Legend: Type --> S - Static, D - Dynamic
Flags --> u - unique, r - registered, e - temporary, c - claimed
a - authoritative, t - route
============================================================================
Intf NextHop Address NBMA Address
Target Network T/Flag
-------- ------------------------------------------- ------ ----------------
Tu1 10.0.0.1 1.1.1.1
10.0.0.1/32 S/
Tu1 10.0.0.4 4.4.4.4
10.0.0.4/32 D/
Spoke1#
Hub1/Spoke1: show ip nhrp summary
Hub1-show ip nhrp summary <click>
Hub1#show ip nhrp summary
IP NHRP cache 3 entries, 1296 bytes
0 static 3 dynamic 0 incomplete
Spoke1-show ip nhrp summary <click>
Spoke1#show ip nhrp summary
IP NHRP cache 3 entries, 1296 bytes
1 static 2 dynamic 0 incomplete
Hub1/Spoke1: show crypto isakmp sa
Hub1-show crypto isakmp sa <click>
Hub1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 1.1.1.1 2.2.2.2 QM_IDLE 1001 ACTIVE 1.1.1.1 3.3.3.3 QM_IDLE 1002 ACTIVE 1.1.1.1 4.4.4.4 QM_IDLE 1003 ACTIVE
Spoke1-show crypto isakmp sa <click>
Spoke1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status 4.4.4.4 2.2.2.2 QM_IDLE 1005 ACTIVE 2.2.2.2 4.4.4.4 QM_IDLE 1004 ACTIVE 1.1.1.1 2.2.2.2 QM_IDLE 1001 ACTIVE
Hub1/Spoke1: show crypto ipsec sa
Hub1-show crypto ipsec sa <click>
Hub1#show crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 1.1.1.1
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (4.4.4.4/255.255.255.255/47/0)
current_peer 4.4.4.4 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 6679, #pkts encrypt: 6679, #pkts digest: 6679
#pkts decaps: 6674, #pkts decrypt: 6674, #pkts verify: 6674
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 4.4.4.4
plaintext mtu 1410, path mtu 1454, ip mtu 1454, ip mtu idb Dialer1
current outbound spi: 0xFE301B66(4264565606)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x9E51C3CB(2656158667)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 19, flow_id: SW:19, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4224637/1606)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xFE301B66(4264565606)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 20, flow_id: SW:20, sibling_flags 80000000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4224633/1606)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (3.3.3.3/255.255.255.255/47/0)
current_peer 3.3.3.3 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 967, #pkts encrypt: 967, #pkts digest: 967
#pkts decaps: 964, #pkts decrypt: 964, #pkts verify: 964
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 3.3.3.3
plaintext mtu 1410, path mtu 1454, ip mtu 1454, ip mtu idb Dialer1
current outbound spi: 0x7DB5DBCE(2109070286)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xC51BF535(3306943797)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 21, flow_id: SW:21, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4164014/1627)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x7DB5DBCE(2109070286)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 22, flow_id: SW:22, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4164010/1627)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
current_peer 2.2.2.2 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 990, #pkts encrypt: 990, #pkts digest: 990
#pkts decaps: 987, #pkts decrypt: 987, #pkts verify: 987
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 1.1.1.1, remote crypto endpt.: 2.2.2.2
plaintext mtu 1410, path mtu 1454, ip mtu 1454, ip mtu idb Dialer1
current outbound spi: 0x2CA3A750(748922704)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x5BE2C5D1(1541588433)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 17, flow_id: SW:17, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4262133/1516)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x2CA3A750(748922704)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 18, flow_id: SW:18, sibling_flags 80004000, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4262129/1516)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Spoke1-show crypto ipsec sa <click>
Spoke1#show crypto ipsec sa
interface: Tunnel1
Crypto map tag: Tunnel1-head-0, local addr 2.2.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (4.4.4.4/255.255.255.255/47/0)
current_peer 4.4.4.4 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 7351, #pkts encrypt: 7351, #pkts digest: 7351
#pkts decaps: 7351, #pkts decrypt: 7351, #pkts verify: 7351
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.2.2, remote crypto endpt.: 4.4.4.4
plaintext mtu 1410, path mtu 1454, ip mtu 1454, ip mtu idb Dialer1
current outbound spi: 0xB760D125(3076575525)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xCC7613FD(3430290429)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 23, flow_id: SW:23, sibling_flags 80004000, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4294357/2554)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0xB760D125(3076575525)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 24, flow_id: SW:24, sibling_flags 80004000, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4294357/2554)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
protected vrf: (none)
local ident (addr/mask/prot/port): (2.2.2.2/255.255.255.255/47/0)
remote ident (addr/mask/prot/port): (1.1.1.1/255.255.255.255/47/0)
current_peer 1.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 997, #pkts encrypt: 997, #pkts digest: 997
#pkts decaps: 998, #pkts decrypt: 998, #pkts verify: 998
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 2.2.2.2, remote crypto endpt.: 1.1.1.1
plaintext mtu 1410, path mtu 1454, ip mtu 1454, ip mtu idb Dialer1
current outbound spi: 0x5BE2C5D1(1541588433)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0x2CA3A750(748922704)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 21, flow_id: SW:21, sibling_flags 80000000, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4284778/1443)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x5BE2C5D1(1541588433)
transform: esp-256-aes esp-sha-hmac ,
in use settings ={Transport, }
conn id: 22, flow_id: SW:22, sibling_flags 80000000, crypto map: Tunnel1-head-0
sa timing: remaining key lifetime (k/sec): (4284782/1443)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
Hub1/Spoke1: show ip interface brief
Hub1-show ip interface brief
Hub1#show ip interface brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0 unassigned YES NVRAM up up GigabitEthernet0/1 192.168.1.254 YES NVRAM up up Dialer1 1.1.1.1 YES IPCP up up NVI0 192.168.1.254 YES unset up up Tunnel0 10.0.0.1 YES NVRAM up up Virtual-Access1 unassigned YES unset up up Virtual-Access2 unassigned YES unset up up
Spoke1-show ip interface brief
Spoke1#show ip interface brief Interface IP-Address OK? Method Status Protocol GigabitEthernet0/0 unassigned YES NVRAM up up GigabitEthernet0/1 192.168.2.254 YES NVRAM up up GigabitEthernet0/2 unassigned YES NVRAM administratively down down GigabitEthernet0/3 unassigned YES NVRAM administratively down down Dialer1 2.2.2.2 YES IPCP up up NVI0 192.168.2.254 YES unset up up Tunnel1 10.0.0.2 YES NVRAM up up Virtual-Access1 unassigned YES unset up up Virtual-Access2 unassigned YES unset up up
ルータ起動から通信できるまでのステータス
Hub1(NHRP_Server)
1–Interface Link UP
%LINK-3-UPDOWN: Interface GigabitEthernet0/0, changed state to up
%LINK-3-UPDOWN: Interface GigabitEthernet0/1, changed state to up
2–Interface Line-Protocol UP
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/0, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface GigabitEthernet0/1, changed state to up
3–Interface Tunnel down
%LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to down
4– CRYPTO OFF
%CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is OFF
%CRYPTO-6-GDOI_ON_OFF: GDOI is OFF
5–Virtual-Access1 UP
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access1, changed state to up
%LINK-3-UPDOWN: Interface Virtual-Access1, changed state to up
6–Virtual-Access2 UP
%DIALER-6-BIND: Interface Vi2 bound to profile Di1
%LINK-3-UPDOWN: Interface Virtual-Access2, changed state to up
%LINEPROTO-5-UPDOWN: Line protocol on Interface Virtual-Access2, changed state to up
7– Tunnel UP
%LINEPROTO-5-UPDOWN: Line protocol on Interface Tunnel0, changed state to up
8– CRYPTO UP
%CRYPTO-6-ISAKMP_ON_OFF: ISAKMP is ON
9–NVI UP
%LINEPROTO-5-UPDOWN: Line protocol on Interface NVI0, changed state to up
10–OSPF LOADING
%OSPF-5-ADJCHG: Process 1, Nbr 192.168.4.254 on Tunnel0 from LOADING to FULL, Loading Done
%OSPF-5-ADJCHG: Process 1, Nbr 192.168.2.254 on Tunnel0 from LOADING to FULL, Loading Done
%OSPF-5-ADJCHG: Process 1, Nbr 192.168.3.254 on Tunnel0 from LOADING to FULL, Loading Done


